Secure by design
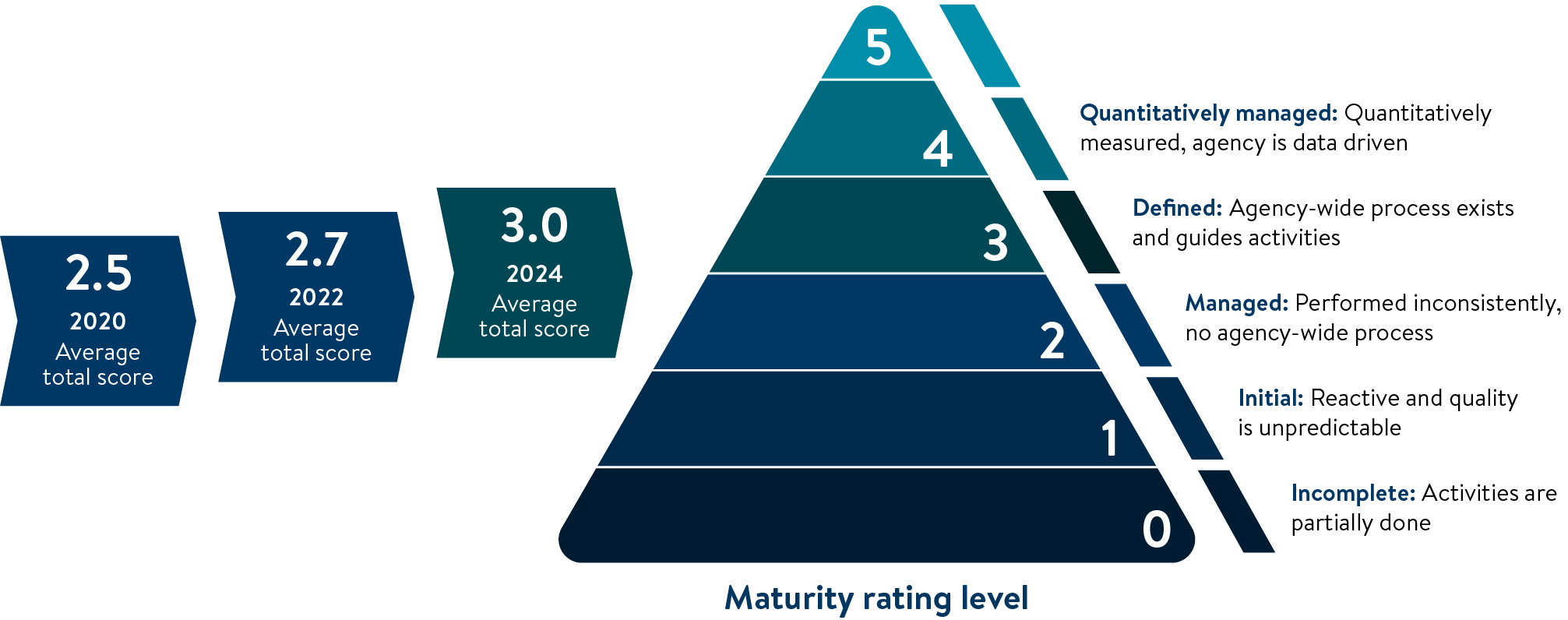
Overview of 2025
MNIT leads a whole-of-state approach to cybersecurity, bringing together individuals, local governments, state agencies, and legislators to defend Minnesota’s digital infrastructure. This shared work protects more than 100,000 system users and the private data of 5.7 million Minnesotans.
MNIT serves as a vital link connecting the state’s counties, cities, townships, public schools, critical infrastructure, and Tribal governments. Together with our federal, state, and local partners, we work to protect Minnesotans’ data and strengthen our shared infrastructure against persistent, ever-evolving cybersecurity threats.
Minnesota delivers a coordinated, whole-of-state approach to bolster cyber resiliency. MNIT and its partners continue to expand collaboration, improve communication, share resources, apply industry best practices, and increase access to advanced tools that help prevent, detect, and respond to cyber threats.
As we navigate the changing cybersecurity landscape, we also partner with the TAC and the Minnesota Cybersecurity Task Force, which brings together a range of public- and private-sector cybersecurity experts. The insights and expertise shared through these partnerships help MNIT better understand emerging needs and opportunities.
MNIT strategically bolsters cybersecurity across Minnesota
MNIT continues to strategically modernize security efforts and expand collaboration with state and local partners across Minnesota. Together, we safeguard data and systems, mitigate risk, and improve organizational effectiveness and customer relationships.
As more state services move online, protecting the digital data Minnesotans rely on remains core to the business of state government. Through key initiatives and day-to-day operations, MNIT continues to mature cybersecurity services and advance strategic goals as it:
- Attracts and retains talent in a highly competitive environment.
- We grew our highly skilled cybersecurity team, adding a cyber threat intelligence lead and a new Security Operations Center (SOC) manager.
- Convenes and leads state, local, territorial, and Tribal (SLTT) entities in Minnesota to build and implement a whole-of-state cybersecurity framework.
- Minnesota Cybersecurity Task Force meets quarterly, with meetings open to the public.
- MNIT hosts a monthly connection meeting with county IT leaders.
- MNIT participates in quarterly Minnesota Indian Affairs Council meetings and provides resources through the Statewide Security Monitoring Initiative and Whole-of-State Cybersecurity Plan.
- MNIT hosts an information-sharing site with 400+ SLTT members and leads monthly sessions where cyber information is shared for awareness and preparedness.
- Embeds a security mindset into everything we do by building expertise across MNIT and the executive branch through training, communications, and engagement.
- Publish quarterly Cybersecurity Monitor newsletter for all state employees in the executive branch to raise awareness of cyber threats, trends, and active security initiatives.
- Send biannual phishing awareness emails to executive branch employees to highlight common tactics and how to recognize and report phishing attempts.
- Reinforce employee skills through regular monthly phishing training campaigns that improve recognition and response confidence.
- Educate the public and state employees in the executive branch during Cybersecurity Awareness Month in October about how to develop strong cyber habits.
- Deliver presentations and participate in public engagements year-round through MNIT’s Cyber Navigator team and other security leaders.
- Require all executive branch employees to complete annual security compliance training.
- Implement an Always Verify (Zero Trust) security framework that authenticates, authorizes, and continuously validates users before granting or maintaining access to applications and data.
- Reduces business impacts when cybersecurity events occur.
- Focus on prevention, preparedness, response, and recovery, to keep operations running.
- Develop and roll out grant-subsidized services to local government entities in Minnesota to bolster their cyber resiliency and protect Minnesotans’ data. MNIT added Next-Generation Security Information and Event Management (Next-Gen SIEM) and Malicious Domain Blocking and Reporting (MDBR) to the three cybersecurity services we began offering in 2024.
- Limit exposure upfront, respond decisively, communicate clearly, and learn fast — turning security from an IT problem into an operational resilience capability.
- Implement a strong third-party risk program to ensure partners and vendors practice strong cyber hygiene as a shared responsibility to protect Minnesota’s data and systems.
- Focus on modernizing tools, processes, and staff skillset to minimize the risk of incidents in this quickly changing cyber landscape.
- Reduce low-value controls and processes to allow greater efficiency for the business to operate.
- Refines operating models, adopts agile approaches, and sets up attribute-driven assessments.
- Use continuous process improvement to enable MNIT to adapt quickly to evolving cyber needs.
- Implement automation where possible to reduce reliance on self-attestation.
- Foster a collaborative product environment that clarifies ownership and decision rights, applies agile delivery, and tracks risk reduction and maturity to enable real-time, data-driven decisions.
Security by the numbers
2
MNIT added two cybersecurity services — Next-Generation Security Information and Event Management, as well as Malicious Domain Blocking and Reporting — for local government partners to strengthen their cyber defenses.
3
Minnesota Cybersecurity Task Force created three subcommittees to provide expertise and actionable strategies.
215
The number of local government entities using MNIT’s managed detection and response (MDR) tool.
269
The number of cyber incidents local governments reported through the new online form.
65,000
The number of endpoints (workstations and servers) that MNIT’s MDR tool protects across Minnesota.
107,000
Cyber threats MDR services detected that had the potential to impact government services.
7M+
The number of security vulnerabilities MNIT resolved across the executive branch.
Millions
MNIT’s MDR tool protects millions of individuals’ sensitive information, from county financial data to public school data.
MNIT reaches new milestone for protecting Minnesotans’ data
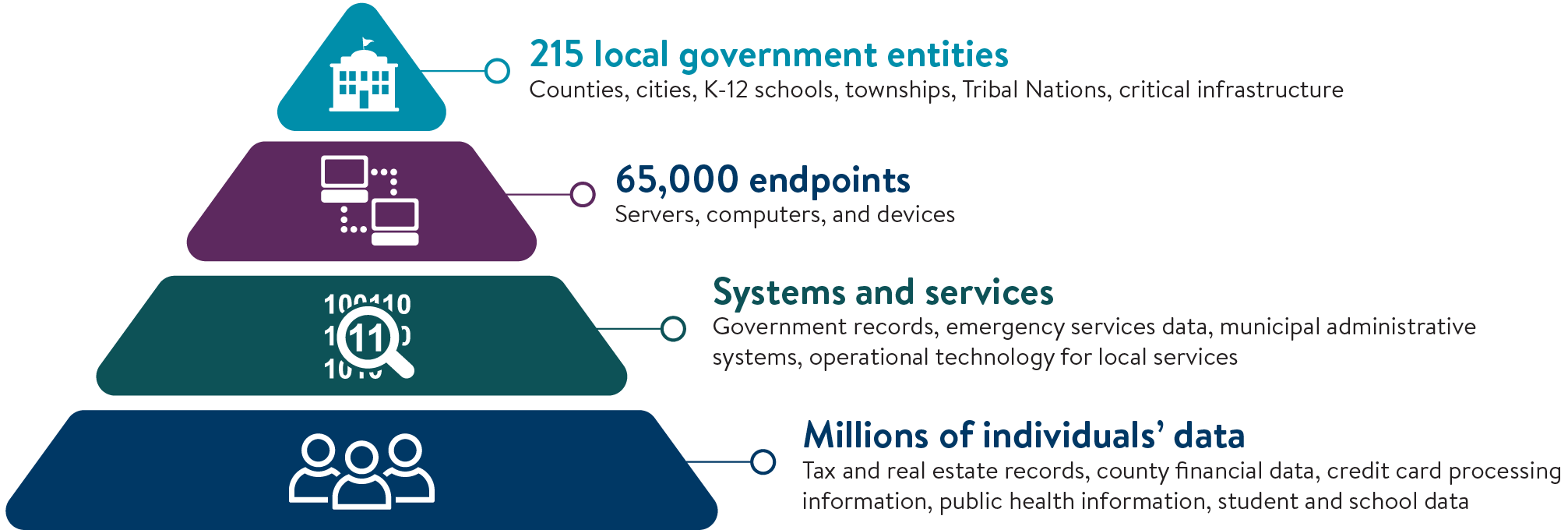
Minnesota’s managed detection and response service now provides 24/7/365 protection to more than 215 local government entities, actively stopping cyber threats before they disrupt services or compromise data. Offered through the Whole-of-State Cybersecurity program, MDR marks a significant milestone in statewide cyber defense.
Counties, cities, K-12 schools, townships, Tribal Nations, and critical infrastructure organizations use MNIT’s endpoint detection and response tools to identify and block attacks that can lead to data breaches, ransomware, and other major incidents. Today, MDR protects more than 65,000 endpoints — workstations and servers across Minnesota — continuously monitoring systems to detect and stop threats before
they cause harm.
This work goes beyond protecting county, city, and public school systems to safeguard the personal information Minnesotans rely on most, including health, tax, and education data. Through MDR, counties and cities protect sensitive information such as property records, infrastructure details, criminal justice files, water system data, and communications with residents. By preventing ransomware and data breaches, MDR keeps critical services online and secure — allowing local governments to serve Minnesotans without disruption.
MNIT’s MDR services detected millions of threats, including more than 107,000 with the potential to disrupt government services. With the average cost of a data breach exceeding $2.8 million, preventing these incidents represents an estimated savings of nearly $300 million for Minnesota government entities.
MNIT detected these threats across 215 local entities and more than 100 executive branch agencies, offices, boards, commissions, and councils — protecting roughly 120,000 endpoints, including more than 65,000 outside Minnesota’s executive branch. MNIT continues to onboard new organizations to the program from the approximately 3,300 eligible entities statewide.
Widespread protection of MNIT’s managed detection and response
CIR law strengthens information sharing, boosts cyber defenses
Minnesota’s cybersecurity incident reporting law gives the state a clearer, faster view of cyber threats by centralizing incident reporting across public entities. This shared intelligence enables MNIT to issue timely threat advisories, support rapid response, and share insights that help Minnesota governments defend against evolving risks.
After the Minnesota Legislature amended state law in 2024, MNIT partnered with the BCA to launch a secure online reporting form for public agencies and government. When the law took effect on Dec. 1, 2024, public entities immediately began using the form to report cybersecurity incidents affecting services, systems, or people.
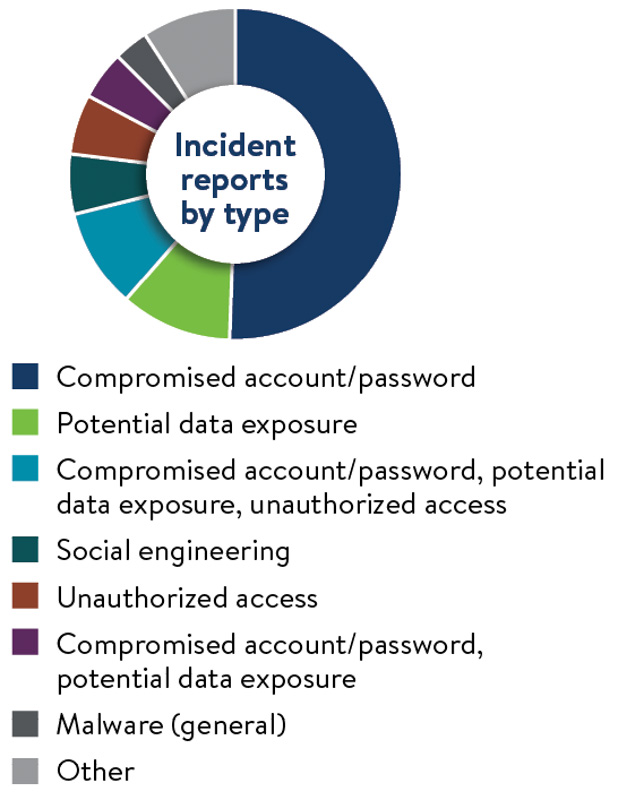
Early reporting reflects a broad cross-section of Minnesota’s public sector and local government partners and captures a wide range of cybersecurity events. In the first year of data collection through the CIR, from Dec. 1, 2024, through Nov. 30, 2025, Minnesota received 334 reports through the CIR online form.
- 283 of the 334 reports were in-scope, meaning they were confirmed cyber events or potential cyber events that affected public agencies or personnel during the reporting period.
- 269 of the 283 in-scope reports were from non-executive branch entities such as counties, cities and K-12 schools.
Data from CIR submissions gives MNIT and its partners clearer insight into who attackers target, which threats continue to emerge, and how cyber incidents affect services and operations. MNIT uses this information to prioritize the tools, resources, and actions that strengthen defenses and prevent future incidents.
As cyber threats evolve, the CIR law continues to serve as a critical foundation for reporting, documenting, responding to, and mitigating incidents. It also strengthens the bridge between state and local partners by improving communication, accelerating information sharing, and reinforcing the collaboration Minnesota relies on to defend against cyber events.
| Type |
Count |
| K-12 |
81 |
| County |
69 |
| City/township |
53 |
| Higher education |
19 |
| Law enforcement |
13 |
| State |
12 |
| Critical infrastructure and key resources |
9 |
| Personal |
8 |
| Nonprofit |
2 |
| Other |
2 |
| Vendor |
1 |
| Total |
269 |
Incident reports by type
Educating state employees and the public
As the information technology agency for Minnesota’s executive branch, MNIT takes seriously its responsibility for protecting the information that Minnesotans entrust to us. Cybersecurity is everyone’s responsibility. We continue to find opportunities to boost awareness and share security tips, resources, and information to protect the State of Minnesota.
Cybersecurity Awareness Month

Governor Tim Walz proclaimed October 2025 as Cybersecurity Awareness Month in Minnesota. Throughout the month, MNIT shared cybersecurity tips publicly and internally to raise awareness about online safety and cybersecurity best practices.
To raise public awareness about online safety, MNIT shared practical cybersecurity tips on social media. These posts covered a range of topics, such as recognizing phishing attempts, securing personal devices, and using strong, unique passwords. The goal was to equip Minnesotans with the knowledge they need to protect their online presence from evolving cyber threats.
For state employees, MNIT launched an internal messaging campaign that reinforced the importance of cybersecurity within the workplace. The campaign focused on educating employees about best practices for securing state systems and data, with clear instructions on reporting suspicious activities. Employees were encouraged to stay vigilant, follow secure communication protocols, and participate in training sessions to understand emerging cyber threats.
This campaign is aided by additional security training for employees like phishing awareness campaigns and federally required annual training. By using public and internal channels, MNIT worked to foster a culture of cybersecurity mindfulness throughout Minnesota, ensuring that residents and state workers remained informed and proactive in protecting digital assets.
Minnesota Military Cyber Symposium

Minnesota’s Chief Information Security Officer (CISO) and MNIT’s Assistant Commissioner John Israel spoke at the second annual Military Cyber Symposium at Metro State University (MSU) in St. Paul on Sept. 13, 2025, organized by the Minnesota National Guard Cyber Coordination Cell (C3). The symposium brought together cyber professionals from around the world, including Minnesota’s State Partnership Program partner nation, Norway. Airmen and soldiers joined state, federal, and international partners, in sharing experiences, best practices, and lessons learned over the last year.
Cyber Security Summit
MNIT leadership and staff were heavily involved in speaking, sharing resources, and leading sessions during the 15th annual Cyber Security Summit in Minneapolis in October.
Public Sector Village
MNIT and the National Guard C3 hosted a Public Sector Village during the Cyber Security Summit to address the broad range of persistent cyber threats that challenge government at all levels. Township, city, county, Tribal, state and federal professionals learned from top security experts about identity protection, Criminal Justice Information Services compliance, cyber insurance, artificial intelligence impacts, and social media risks. Participants explored the cybersecurity tools and shared services available to Minnesota’s public entities, as well as how to leverage no cost and discounted resources for detection, response, and incident support.
Building a cybersecurity program
MNIT Governance, Risk, and Compliance Policy Lead Ron Olsen led the Cyber 101 sessions “Building Blocks: Developing a Comprehensive Cybersecurity Program.” He explained how to build a strong cybersecurity program through standards, governance, and strategic alignment. The session covered risk mitigation, accountability frameworks, and oversight processes to help organizations enhance resilience, protect assets, and align cybersecurity efforts with business goals in today’s evolving threat landscape.
Highlighting state careers
During the Summit’s careers breakfast for students and seasoned cyber professionals, MNIT leaders — Minnesota’s CISO and MNIT Assistant Commissioner John Israel, Minnesota’s Deputy CISO Jen VanDemmeltraadt, and MNIT’s Director of Agency Strategic Security Chris Luhman — shared information and offered insight on cybersecurity careers within the State of Minnesota.
Educating future tech leaders
Students and teachers from Wayzata Public Schools visited MNIT to explore the wide range of career opportunities in technology and cybersecurity within state government. The visit gave students a first-hand look at how IT professionals protect digital systems, build accessible services, and use data and innovation to improve how state government serves Minnesotans. Technology careers in state government span areas like software development, cybersecurity, data science, user experience, and IT infrastructure — offering meaningful, mission-driven work that makes a difference every day.
Being prepared led to a quick, unified response to cyberattack
Federal, state, and local governments continue to rise in both frequency and sophistication of cyberattacks. These attacks disrupt critical services, steal data, and lead to ransomware, raising serious safety and security concerns for the public. The cyberattack that targeted the City of St. Paul’s critical systems and digital services in July caused significant disruptions. This cyberattack is not unique — other cities, counties, and schools have experienced similar incidents in the past year. These incidents underscore the need to work together, share resources, strengthen security programs, and build a strong cybersecurity culture across Minnesota.
The portion of the City of St. Paul’s computers that were enrolled in MNIT’s MDR program performed as expected — MDR detected the malicious activity and alerted city officials. The city’s systems that were compromised in the cyber incident were not part of MNIT’s MDR program. During the Minnesota Cybersecurity Task Force’s November meeting, City of St. Paul officials credited the task force and MNIT
for having the foresight to establish the MDR program, saying it had proven its strength to detect cyber threats.
The magnitude and complexity of the cybersecurity incident exceeded the city’s response capacity, and St. Paul officials closely coordinated with MNIT and an external cybersecurity vendor. Governor Tim Walz issued an executive order activating the Minnesota National Guard cyber protection teams — for the first time in state history — to address the incident and ensure vital municipal services continued. Together, the city, MNIT, National Guard, and other state and federal entities worked around the clock to ensure continuity of vital services and the safety and security of St. Paul residents.
Protecting the technology, data, and systems that make our government and schools run is one of our highest priorities. MNIT helps public entities protect their technology, data, and systems to keep them running securely. We provide local entities, Tribal Nations, public schools, public health, critical infrastructure, and peacekeepers the cybersecurity tools and resources they need at no or low cost. MNIT’s whole-of-state approach uses state funding and federal grants to protect Minnesotans’ data by advancing stronger, sustainable cybersecurity tools and processes that leverage best practices, build on past successes, and meet every organization where they are at.
We have seen the value of building trusted partnerships among all levels of government, through sharing communication, information, and support. The steps state and local government entities have taken to prepare and defend data and networks has proven to make a difference.
St. Paul continues its recovery efforts
The July cyberattack on the City of St. Paul reflects a broader rise in ransomware attacks affecting government at all levels, as well as organizations across every sector. The City’s quick, decisive response limited the impact, protected critical services, and positioned its systems for a safe and secure recovery.
City leaders provided ongoing communication and transparency, brought in state and federal partners, and shared information with them, resulting in a collaborative response and recovery effort. The National Guard’s Cyber Protection Team provided 17 consecutive days of support in its first mobilization, strengthening the city’s efforts. City leaders have openly shared lessons learned to help other local governments build their defenses and prevent a similar cyberattack. Since then, MNIT has seen an increase in the number of public entities using MNIT’s MDR services.
Attack details
- Date detected: July 25, 2025
- Method of detection: The city’s computer systems enrolled in MNIT’s MDR program were the first to detect and alert city officials to the malicious activity.
- Attackers: Interlock ransomware group.
- Data stolen: About 43 gigabytes of data from a Parks and Recreation network drive.
- Data leaked: After the city refused to pay the ransom, cybercriminals posted data publicly. A forensic review is ongoing, and the City is following all legal and regulatory requirements for notification.
Key metrics and impact
- City response: Shut down networks, deactivated compromised accounts, isolated affected servers, ensured critical public safety services continued without interruption, completed a password reset and device check for over 3,000 city employees, offered city employees 12 months of identity theft protection, increased monitoring across city systems, engaged national incident response firm, and worked with federal and state agencies.
- System recovery: Recovery focused on restoring critical services first, ensuring each system was secure, stable, and ready for long-term use.
- Services affected: Internet in city buildings, library WiFi, some phone lines, and online payments for some services.
- Services unaffected: Emergency services, including 911, remained operational throughout the incident.
- Financials: Full cost to be determined.
Ongoing actions
- Lessons learned shared with other municipalities.
- Focus on strengthening defenses, backups, and staff training.
- Accelerate modernization and resilience efforts to strengthen its long-term cybersecurity posture.
Minnesota enhances cybersecurity defenses with GovRAMP partnership
As cybersecurity threats become increasingly sophisticated, the State of Minnesota has partnered with GovRAMP to reduce risk, improve operational efficiency and secure public data. Minnesota upholds the integrity of its systems and the public’s trust through the enforcement of rigorous security standards, compliance protocols, and vendor accountability. GovRAMP supports this work by offering a standardized framework to assess the cybersecurity readiness of cloud solutions who handle highly sensitive data. Modeled after FedRAMP, it provides a framework for ongoing monitoring and evaluation of cloud service providers.
A key part of this partnership involves proactively identifying, assessing, and reducing potential threats from cloud-based vendors that handle highly sensitive — or high-categorized — state data. Managing this risk helps ensure the technology that is procured meets trusted security benchmarks. Without strong oversight, these cloud-solution relationships can expose Minnesota systems to significant vulnerabilities and cybersecurity threats.
MNIT worked with GovRAMP to notify and educate affected vendors of the state’s partnership and forthcoming requirements.
-
Beginning Oct. 1, 2025
Existing State of Minnesota contracts with cloud-based vendors handling high-categorized data now have GovRAMP requirements added during amendments or renewals, and new contracts will include the requirements.
-
Effective April 1, 2027
All cloud-based vendors — new and existing — handling Minnesota’s high-categorized data must be GovRAMP authorized. The 18-month timeframe allows vendors sufficient opportunity to understand the new contract requirements and complete the GovRAMP authorization process.
This forward-looking partnership enhances data protection and ensures that cloud solutions entrusted with Minnesota’s most sensitive data meet our rigorous cybersecurity standards. Together, we’re creating a safer digital environment for the people we serve.
MNIT teams resolve 7+ million security vulnerabilities through TVMU
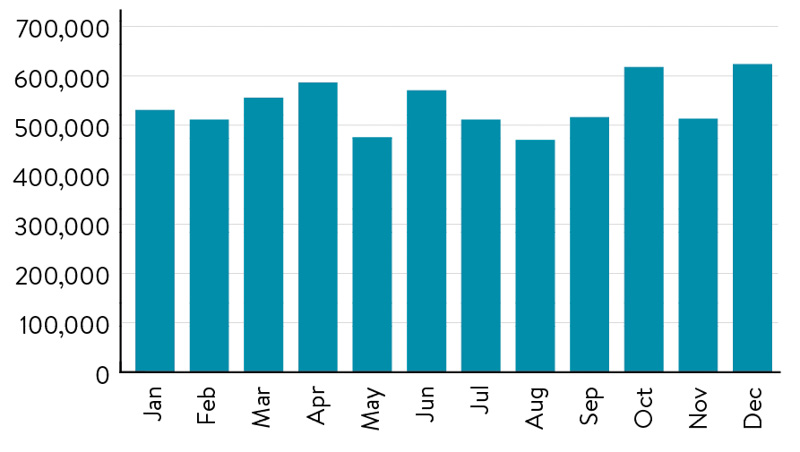
New security vulnerabilities come out on a daily basis, so vulnerability and patch management is an ongoing and necessary process for organizations. MNIT’s Threat and Vulnerability Management Unit (TVMU) uses sophisticated tools to continuously scan for new software or hardware flaws on state accounts and devices — including a range of computing platforms, including desktops, servers, and network devices. After TVMU identifies flaws or security vulnerabilities, MNIT works with state agencies to help remediate these issues and reduce agencies’ cybersecurity risks. MNIT resolved 7,029,450 million security vulnerabilities across the executive branch in 2025. This proactive work helps reduce the risk of security breaches, data loss, and other security incidents.
Threat and vulnerability instances identified in 2025
BISOs partner with agencies to ensure security, business goals align
MNIT updated its organizational structure to better serve Minnesotans and our partnering agencies. The reorganization included standardizing the role of MNIT’s five Business Information Security Officers (BISOs). They are the main liaisons between state agency partners and MNIT security leadership. BISOs help agencies do business safely. They manage cybersecurity strategy, governance, and risk management, while ensuring security objectives align with business goals. Each BISO is accountable for coordinating security across multiple agencies and ensuring alignment with enterprise security policies, while addressing agency-specific risks.
Statewide account security update with multi-factor authentication
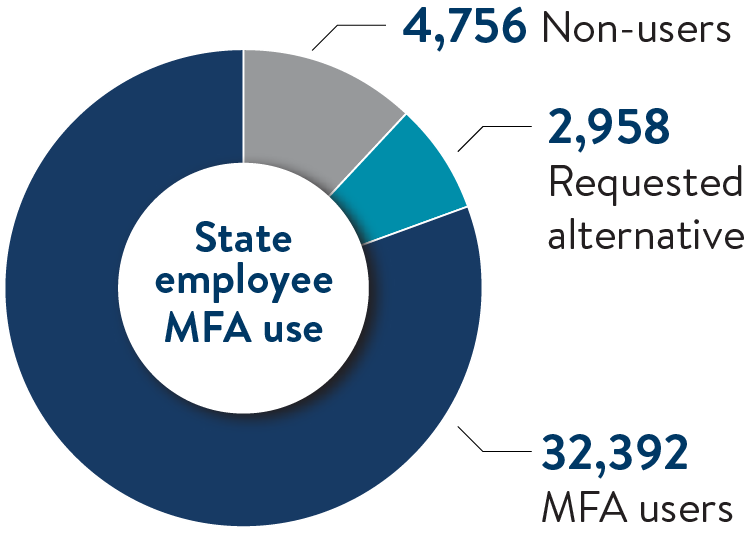
State employee MFA use
In 2025, MNIT completed a major statewide effort to strengthen how State of Minnesota employees securely access their work accounts. The project expanded the use of multi-factor authentication (MFA), a security step that asks users to verify their identity in addition to entering a password. This verification may include a prompt on a mobile app or the use of a physical security key.
MFA had been available to state employees for several years as an optional tool through the vendor. As cyber threats increased and national security standards evolved, MNIT identified the need for a consistent approach to account security across the executive branch.
MNIT launched an enterprise project to require MFA for all executive branch employees and to roll out an authenticator app statewide. Based on lessons from earlier modernization efforts, the project emphasized clear communication, advance notice, and user readiness. MNIT worked closely with agencies to schedule phased rollouts, identify blackout dates, and avoid interruptions to critical business operations.
The project team also addressed different workplace needs. For staff who could not use a mobile app, MNIT provided alternatives such as physical security key fobs. Agencies received step-by-step instructions, access to office hours, and support from the Enterprise Service Desk to help employees prepare and troubleshoot issues. What began as an optional security feature is now a routine part of daily work, helping keep state systems, and the services Minnesotans rely on, secure and reliable.
Today, about 80% of state employees use MFA to protect their accounts. In addition to specialized accounts, some users work in locations or roles with restrictions on what they can use to verify their identity. MNIT is working with agencies to identify approved solutions for these locations and continue progress toward full multi-factor authentication coverage.
Cybersecurity metrics
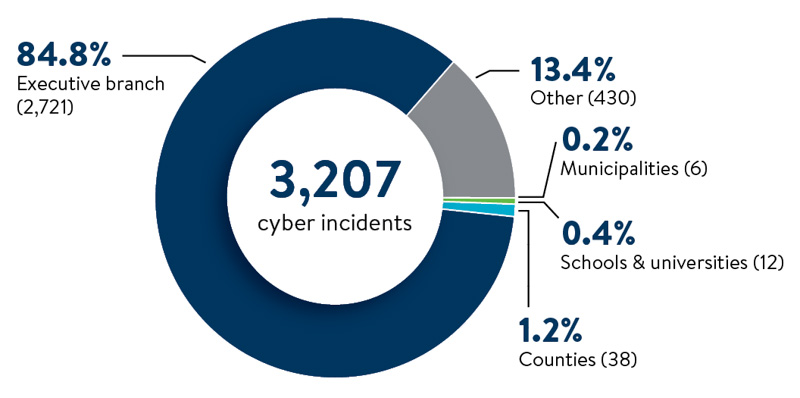
To keep state government running and protect Minnesotans’ private data, we must continually work to better secure Minnesota’s IT systems. In 2025, our Security Operations Center (SOC) detected or received reports of 3,207 cyber events.
| Type of cyber event |
# reported |
| Compromised account |
140 |
| Compromised password |
489 |
| Copyright violation |
4 |
| Denial of service |
10 |
| Inappropriate use |
7 |
| International travel requests |
339 |
| Lost/stolen device |
67 |
| Malware |
1,197* |
| Network attack/scan |
7 |
| Operational |
18 |
| Policy violation |
697 |
| Ransomware |
3 |
| Social engineering |
135 |
| Threat intelligence |
11 |
| Unauthorized access attempt |
18 |
| Unauthorized disclosure |
11 |
| Other |
54 |
| Total |
3,207 |
*MNIT’s MDR tool classifies a broad range of events as malware — some of which may have been categorized differently if detected manually by the SOC. We continue to refine our analysis and improve our ability to interpret SOC data effectively.
Cyber events investigated by MNIT for all Minnesota government partners in 2025
 4.74
4.74  316
316 500+
500+  5,709
5,709  3,049
3,049  2,861
2,861  1,053
1,053  3,207
3,207  465,280
465,280  6,220,867
6,220,867  56,103,542
56,103,542  409,263,840
409,263,840 134,900,000+
134,900,000+ 113,268,630
113,268,630 101,600,787
101,600,787